Node.js, one of the leading JavaScript runtimes, is capturing market share gradually.
When anything becomes popular in technology, they are exposed to millions of professionals, including security experts, attackers, hackers, etc.
A node.js core is secure, but when you install third-party packages, the way you configure, install and deploy may require additional security to protect web applications from hackers. To get an idea, 83% of Snyk users found one or more vulnerabilities in their applications. Snyk is one of the popular node.js security scanning platforms.
And another latest research shows ~14% of the whole npm ecosystem was affected.
In my previous article, I mentioned finding security vulnerabilities in a Node.js application, and many of you asked about remediating/securing them.
Best Practices for Improving Node JS Security
No framework, including Node JS, could be cited as 100% secure. Hence, you must follow these security practices to avoid risks.
- Regularly log and monitor activities to detect vulnerabilities
- Do not block the Event Loop
- Use flat Promise chains to avoid nesting layer errors
- Create strong authentication policies for your ecosystem
- Manage errors to prevent unauthorized attacks
- Use anti-CSRF tokens in your applications
- Stop data leakage by sending only the essential information
- Properly manage sessions with cookie flags
- Control request size to prevent DoS attacks
- Use customized package settings and a non-default user password
- Implement access control rules for each request
- Regularly update packages to stay secure against threats and attacks
- Protect from web security vulnerabilities using appropriate security headers
- Do not use dangerous functions for the sake of application stability
- Use strict mode to avoid errors and bugs
Now, we explore the best tools to secure NodeJS applications.
Snyk
Snyk can be integrated into GitHub, Jenkins, Circle CI, Tarvis, Code Ship, and Bamboo to find and fixes known vulnerabilities.
You can understand your application dependencies and monitor real-time alerts when risk is found in your code.
On a high level, Snyk provides complete security protection, including the following.
- Finding vulnerabilities in the code
- Monitor code in real-time
- Fix the vulnerable dependencies
- Get notified when a new weakness impacts your application.
- Collaborate with your team members
Snyk maintains its own vulnerabilities database, and currently, it supports Node.js, Ruby, Scala, Python, PHP, .NET, Go, etc.
Jscrambler
Jscrambler takes an interesting, unique approach to provide code & web page integrity on the client side.
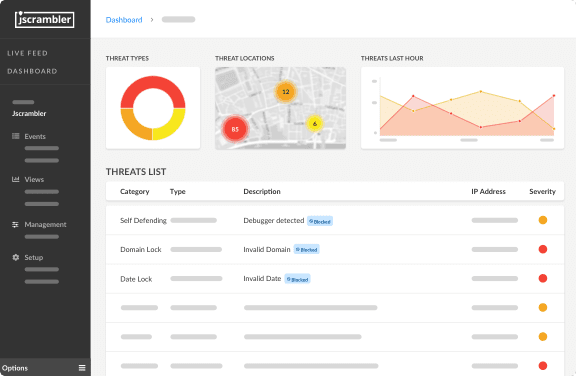
Jscrambler makes your web application self-defensive to fight fraud, avoid code modification in run-time, and data leakage, and protect from reputational loss and business.
Another exciting feature is application logic, and data is transformed so that it’s hard to understand and hidden on the client side. This makes it difficult to guess the algorithm, technologies used in the application.
Some of the Jscrambler featured include the following.
- Real-time detection, notification & protection
- Protection from code injection, DOM-tampering, man-in-the-browser, bots, zero-day attacks
- Credential, credit card, private data loss prevention
- Malware injection prevention
Jscrambler supports most JavaScript frameworks such as Angular, Ionic, Meteor, Vue.js, React, Express, Socket, React, Koa, etc.
So go ahead and give a try to make your JavaScript application bulletproof.
Cloudflare WAF
Cloudflare WAF (Web Application Firewall) protects your web applications from the cloud (network edge). You don’t have to install anything in your node application.
There are three types of WAF rules you get.
- OWASP – to protect an application from OWASP top 10 vulnerabilities
- Custom rules – you can define the rule.
- Cloudflare specials – Rules defined by Cloudflare based on application.

By utilizing Cloudflare, you don’t add security to your site and take advantage of their fast CDN for better content delivery. Cloudflare WAF is available in the Pro plan, which costs $20 per month.
Another cloud-based security provider option would be SUCURI and StackPath, a complete site security solution to protect from DDoS, malware, known vulnerabilities, etc.
Helmet
Different tools are available in the market today, and that’s where startups and young professionals get confused about which one someone should choose for their particular job. Here, I present, Helmet.JS! Helmet is based on the Node.JS module.
Its essential deliveries include enhancing the security of applications by configuring HTTP Headers and guarding against potential online threats like Cross-Site Scripting and clickjacking attacks.
Its built-in modules are convenient and deliver a proper security backup. Some of the modules I found to be sharable are mentioned below:
- Content-Security-Policy
- X-Frame-Option
- Public-Key-Pins
- Cache-Control
- Referrer-Policy
- X-XSS-Protection
Overall, I find this tool deserves to be on the list because of the aspects it covers concerning security.
N|Solid
N|Solid is a drop-in replacement platform to run a mission-critical Node.js application.

It got inbuilt real-time vulnerability scanning and custom security policies for enhanced application security. You can configure it to get alerted when a new security vulnerability is detected in your Nodejs applications.
Rate Limit Flexible
Use this tiny package to limit the rate and trigger a function on the event. This will be handy to protect from DDoS and brute force attacks.
Some of the use cases would be as below.
- Login endpoint protection
- Crawler/bot rate limiting
- In-memory block strategy
- Dynamic block based on the user’s action
- Rate limiting by IP
- Block too many login attempts
Wondering if this will slow the application?
No, you won’t even notice that. It’s fast; the average request adds 0.7ms in the cluster environment.
AppTrana Cloud Waap (WAF)
AppTrana has been considered a completely administered WAF solution. It can provide an end-to-end security solution concerning a web application. It’s well-known for its attractive services and features, some of which are noted below:
- Threat-based security: For the purpose of protecting the web application, as mentioned above, AppTrana uses a specific and significant risk-based approach. Along with the protection of bot mitigation service, It can serve excellent security from API risks and DDoS attacks. Additionally, it aids in ensuring excellent performance as well as non-stop availability.
- Identification of vulnerability: In order to detect the vulnerabilities, AppTrana combines manual penetration testing that includes human security experts for regularly testing the application to identify potential vulnerabilities with automated scanning tools that have the capability of identifying common security threats.
- Web Acceleration with Secure CDN: In addition to security, AppTrana prioritizes web acceleration through the deployment of a Content Delivery Network (CDN). CDN services improve website performance by caching content closer to end users, lowering latency, and increasing response times. AppTrana’s CDN is built to work safely alongside the WAF features.
Looking at its services and features. I believe this tool deserves the spot on the list. I recommend using AppTrana; if you want to secure your app and get the outcomes of your wish, switch to AppTrana!
RASP (Runtime Application Self Protection)

A lot of organizations are running behind security concerns and their solutions. Various tools have been developed to help organizations find vulnerabilities and security loopholes. The list includes tools to help organizations and startups secure their web applications. We have “RASP (Runtime Application Self Protection)” among them!
This tool is an excellent option for organizations. It protects cloud-native applications from vulnerabilities and provides security from within, ensuring application safety.
RASP has a brilliant attack detection feature, which means RASP can detect and protect against attacks in real time. The tool is like armor that can protect from attacks like clickjacking, unvalidated redirects, malformed content types, etc.
This is not just enough! It watches out for your back by giving you support on your web applications weaknesses as well. RASP can be integrated with Active applications, Third-Party Applications, API, Cloud Applications, and Microservices.
To be honest, I felt this tool could secure your web application with its dual effect of WAF and RASP, which potentially means defense in depth. Its fantastic and much-needed features are attractive enough for startups and organizations to make their web applications secure and help them easily find vulnerabilities.
DOMPurify
The following tool is not fast; it’s just super fast! Developers call it sanitizer, as it’s a reliable tool to secure your Node.js Application. DomPurify prevents XSS attacks & other vulnerabilities and proves itself an emerging star in the developer’s community.
The main attraction toward this tool is its speed and ease of use. It’s swift in scanning, detecting, and eliminating security threats for your application. DOMPurify works server-side with Node.js. Therefore the installation is straightforward and handy.
To proceed with DOMPurify, you need to install “jsdom” first. I would recommend using this tool if you want to enhance your security and beat down the heat of significant security threats.
Conclusion
I hope the above list of security protection helps you to secure your NodeJS application.
Next, don’t forget to check out the monitoring solution.


















