AWS Secrets Manager allows you to securely store all your credentials, data, passwords, and other secrets.
Cyberattacks are increasing rapidly across the globe, aiming to steal confidential information and money and leaving organizations devastated.
This is why there is a need to use strong services like Secrets Manager that can protect your data.
In this article, I’ll discuss AWS Secrets Manager and how beneficial it can be for you.
Let’s start!
What Is AWS Secrets Manager?
AWS Secrets Manager is a tool that helps users manage, rotate, and retrieve their secrets, like passwords, API keys, database and application credentials, etc., throughout each one’s lifecycle.
A secret here can be a confidential, valuable piece of information about your organization that you want to store securely. It can be a credential like a password and a user name, an OAuth token, an AWS credential, SSK keys, encryption keys, certificates and private keys, and more.
The main aim of AWS Secrets Manager is to manage and safeguard your data used for accessing IT resources, services, applications, and systems. It stores and manages secrets and data in a centralized place, making it easier for legitimate users to access them without requiring complex code.
AWS Secrets Manager allows you to rotate secrets across various AWS services like Redshift, RDS, and DocumentDB. This enables all the keys and database credentials to be updated constantly across those services. In addition, you can rotate secrets on demand or on a schedule using the tool’s in-built console, AWS SDK, or AWS CLI.
Moreover, AWS Secrets Manager provides better data control and strong encryption for data protection. It also allows you to monitor your protected information and audit it with the help of various integrations available.
Its biggest users are large businesses with respect to business size and software companies with respect to industry type.
AWS Secrets Manager: Features
#1. Secret Storage and Management
Not only storage, but you can also manage your secrets easily with Secrets Manager. To manage data on the platform, you can perform various actions with your data:
- Creating a secret and database
- Modifying a secret
- Finding a secret
- Deleting a secret that you no longer require
- Restoring a secret that you have lost or deleted
- Replicating a secret to another AWS region
- Promoting a replicated secret to a given standalone secret within AWS Secrets Manager
You can store your credentials on the platform after creating your account in Amazon Aurora, Amazon RDS, Amazon DocumentDB, or Amazon Redshift. You can do it by using the Secrets Manager console, AWS SDK, or AWS CLI.
#2. Strong Security

AWS Secrets Manager uses strong encryption to safeguard all your secrets from unauthorized users. It encrypts your secrets using AWS Key Management Service (KMS) keys.
Secrets Manager utilizes AWS Identity and Access Management (IAM) to allow users to access their secrets securely. It offers advanced access controls and authentication.
- Authentication is used for verifying the identity of the user making the request. And the identification is done through a sign-in process requiring multi-factor authentication (MFA) tokens, access keys, and passwords.
- Access control is used to ensure that approved users can only perform certain operations on secrets.
Apart from these, Secrets Manager makes use of policies defining which users can access what resources and take which actions on those secrets or resources. It lets you use AWS IAM Roles Anywhere and gain temporary credentials for security in IAM for servers, applications, containers, and other workloads running out of AWS.
In addition, you can enable the same IAM roles and policies for your workloads that you have created for AWS apps to access your resources in both AWS and on-premises devices (like application servers).
#3. Secrets Rotation

AWS Secrets Manager allows you to rotate secrets on a schedule or on demand without disrupting or redeploying your active applications.
Here, secrets rotation refers to the process of updating an organization’s secrets periodically. So, when you rotate a given secret, you will need to update the data or credentials in the secret as well as the service or database. In addition, it lets you automate secret rotation and save time by setting up and automating secrets rotation via the console and AWS CLI to save time.
To update a secret, AWS Secret Manager leverages the function AWS Lambda and calls it based on the set-up schedule. For this, you will need to set up a specific schedule to enable rotation after a certain period, like 90 days or 30 days. It can also be done by creating a cron expression.
Moreover, the Secrets Manager can label the version of the secret during rotation by using staging labels. It can call a function many times during rotation by giving different parameters.
Here’s how you can rotate a secret:
- Create the secret’s new version. It can have a new username and password along with more secret data.
- Change the existing credentials in the service or database. Doing this will match new credentials in the new secret version. Based on the rotation strategy you are implementing, a new user will be created having the same access permissions as that of the existing user.
- Test the newly created secret version by allowing it to access the service or database. Based on the access type that your applications require; you can include read and write access.
- Perform the rotation by moving the new version from the old version to the new secret version. Retain the old version and add it to the previous version to avoid losing the secret altogether.
#4. Secret Monitoring

Since breaches and inefficiencies can happen at any time, it’s important to keep an eye on your secrets and take needed actions when there’s still time. AWS Secrets Manager allows you to monitor your data using monitoring tools and immediately report in case something goes wrong.
You will be able to use logs to investigate any unexpected changes or usage. If found, you can also roll back the unwanted changes and retrieve the previous version. In addition, you can configure automated checks to detect any attempt to secret deletion or inappropriate secret usage.
Here’s what you will get with secret monitoring:
- Log events using AWS CloudTrail: AWS CloudTrail can record API calls as events from the console for secret rotation and deletion. It will show you recorded events from the last 90 days. You can also set up CloudTrail to deliver log files directly to Amazon S3 bucket from multiple AWS regions and accounts.
- Monitor using CloudWatch: With CloudWatch, you can easily monitor your secrets by letting it collect and process raw data into real-time, readable metrics. The data will be saved for 15 months to gauge your service or app’s performance.
- Match the events using EventBridge: With EventsBridge, it’s possible to match events from AWS CloudTrail log files. For this, configure the riles looking for those events and send a new event to take action to a target.
- Monitor scheduled secrets for deletion: By combining Amazon CloudWatch Logs, Simple Notification Service (SNS), and CloudTrail, you can set up alarms to notify in case of any unauthorized attempt to delete a secret.
Upon receiving an alarm, you will have the time to think whether you really want to get it deleted or stop deletion. Alternatively, you can allow a user to use a new secret and provide them with access permissions.
#5. Integrations
AWS Secrets Manager integrates with plenty of other Amazon and AWS tools. The list includes Alexa for Business, AWS App2Container, App Runner, Amazon AppFlow, AWS AppConfig, Amazon Athena, Amazon DocumentDB, AWS DataSync, AWS CodeBuild, Amazon ElasticCache, Amazon EMR, AWS Elemental Live, Amazon QuickSight, Amazon Redshift, AWS Migration Hub, Amazon RDS, and more.
Why Use AWS Secrets Manager

Enhanced Security Posture
Secrets Manager enables you to enhance your organization’s security posture since you don’t need any hard-coded credentials in your application’s source code. By storing your credentials in the Secrets Manager, you can avoid security-related compromises by someone who can access the app or its components.
Disaster Recovery
A disaster can knock on your door at any time, such as a cyber breach. This will lead you to lose your crucial information, passwords, and other credentials and data. Or, you might lose your data due to accidental deletion.
Using the tool, you can replace your hard-coded credentials with a call in the runtime to the AWS Secrets Manager in order to dynamically retrieve your credentials when in need.
Reduced Risks

Secrets Manager lets you configure a rotation schedule so that the secrets can rotate automatically when the time comes. This way, you can replace your long-term secrets with short-term secrets, which helps reduce the risks of security compromises.
In addition, rotating credentials doesn’t require application updates or modifying application clients since you won’t store your credentials with the application.
Meeting Compliance Requirements
Looking at the increasing security and privacy risks, regulatory bodies like GDPR and HIPAA require organizations to adhere to their compliance standard to ensure they are handling customer and business data securely. Thus, use only an application or service that’s safe and compliant with applicable regulations.
AWS Secrets Manager, you can monitor your secrets to detect any security vulnerability or risk that can compromise your data and take action beforehand. This essentially safeguards your business and customer information, which is highly crucial to maintaining compliance. You can also better prepare yourself for audits by documenting everything.
Furthermore, you can leverage AWS Configs to assess your secrets and how their compliance with your organization’s internal policies, regulations, and industry guidelines. It lets you define compliance requirements and internal controls for secrets and identify secrets that aren’t compliant.
Better Controls

You will get better control of your secrets, systems, and other data with fine-grained policies and access controls. AWS IAM will ensure the right person has the right level of access permissions to the right resources. Administrators can create or delete accounts, allow or restrict access to users, add or remove members, and perform many actions based on the needs and situations.
AWS Secrets Manager: How to Setup and Use it
Here’s how you can set up and use AWS Secrets Manager:
- Set up your AWS account by entering the required details.
- Log in to your AWS account
- Go to the AWS Secrets Manager console
- Locate the “Store a new secret” option and click on it to create and store your secret.
How to Create and Store a New Secret
For creating a secret in Secrets Manager, you require permission from the SecretsManagerReadWrite managed policies. When a secret is created, Secret Manager will generate a CloudTrail log entry.
Follow the below steps to store your access tokens, API keys, and credentials in AWS Secrets Manager:
1. Open the AWS Secrets Manager console
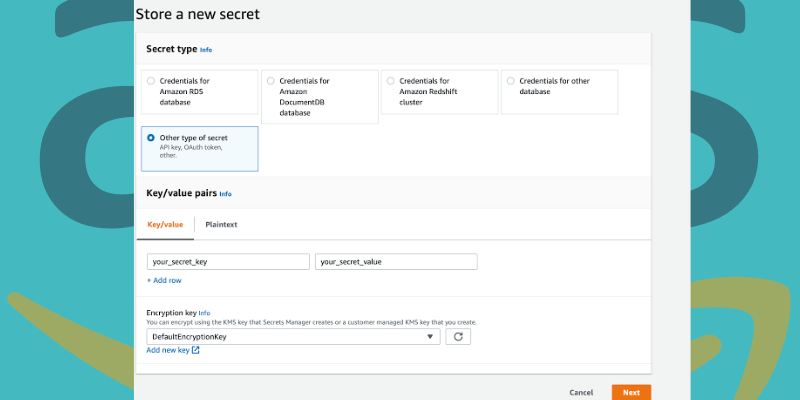
2. Click on “Store a new secret”.
You will find the page “Choose secret type”. Next, perform the following steps:
- Select “Other type of secret” for the type of secret you want to create.
- You will see Key/value pairs. Enter a secret in key/value pairs in JSON. Or, select the tab Plaintext and enter your secret in a format of your choice. It’s possible to store secrets up to 65536 bytes.
- Select the AWS KMS key used by Secret Manager to encrypt the secret value. Mostly, you can go for
aws/secretsmanagerfor using the managed key. It incurs no cost. - To access a secret from a different AWS account or use your KMS key to enable rotation or implement a policy to this key, select “Add new key” or select a key that’s customer managed from the given list. However, a customer-manged key is paid.
- Select “Next”
3. From the page “Configuration secret”,
- Enter a Secret name and its description. The name must have 1-512 Unicode characters.
- You can add tags to a secret from the Tags section. You can also include a resource policy by choosing “Edit permissions”.
- In addition, it’s also possible to replicate a secret to a different AWS region by choosing “Replicate secret”. These steps are optional.
- Choose “Next”
4. If you want, you can enable automatic rotation from the page “Configuration rotation”. This step is also optional. Choose next.
5. Review the secret’s details from the “Review” page and select “store”. And you are done; the Secret Manager will return to the secrets list. You must see the newly added secret there; if not, refresh.
Apart from the console, you can also add a secret through AWS SDK and AWS CLI.
AWS Secrets Manager vs. AWS Parameter Store
AWS Parameter Store is an application management tool by AWS Systems Manager (SSM) that allows users to create a key-value parameter, which can save an application’s configurations, credentials, product keys, and custom environment variables.
On the other hand, AWS Secrets Manager is a service that lets you create, store, manage, retrieve, and rotate credentials, keys, API tokens, etc.
Both these services have similar interfaces where it’s easy to declare your key-value pairs for secrets and parameters. However, they do on the following grounds:
| AWS Secrets Manager | AWS Parameters Store | |
| Storage size | Stores up to 10 kb of secret size | Stores up to 4096 characters or 4 kb for an entry and can go up to 8 kb for advanced parameters |
| Limits | Can store 500k secrets/region/account | Can store 10,000 standard parameters/region/account |
| Cost | It’s paid, costing $0.40/secret/month | Free for standard parameters and costs $0.05/10,000 API calls for advanced parameters |
| Rotation | Offers automatic rotation for any secret at any time and can be configured | You will need to write a function by yourself to update credentials |
| Cross-account access | Yes | No |
| Cross-region replication | Yes | No |
| Type of credentials | It’s for confidential data that needs encryption, so, limited use cases. | Wider use case since you can store more types of credentials including app configuration variables like product keys, URLs, etc. |
Conclusion
Whether you are from a small, medium-sized, or large business, you can use AWS Secrets Manager to create and store your secrets. It offers enhanced security, privacy, access controls, features, and capabilities to safeguard your secrets from unauthorized access.
You may also explore how to perform AWS Security Scanning and configuration monitoring.



















