After an in-depth lookup at the present scenario, the rate at which the world is growing and moving ahead is pretty unimaginable, and tech’s role is never excludable.
As long as tech evolves, we will never face a shortage of new inventions and discoveries like AI. But this change brings a lot of uncertainty among the tools and mediums we as a developer need to crack for the advancements. Among these circumstances, Python, a programming language, is still standing solid & straight.
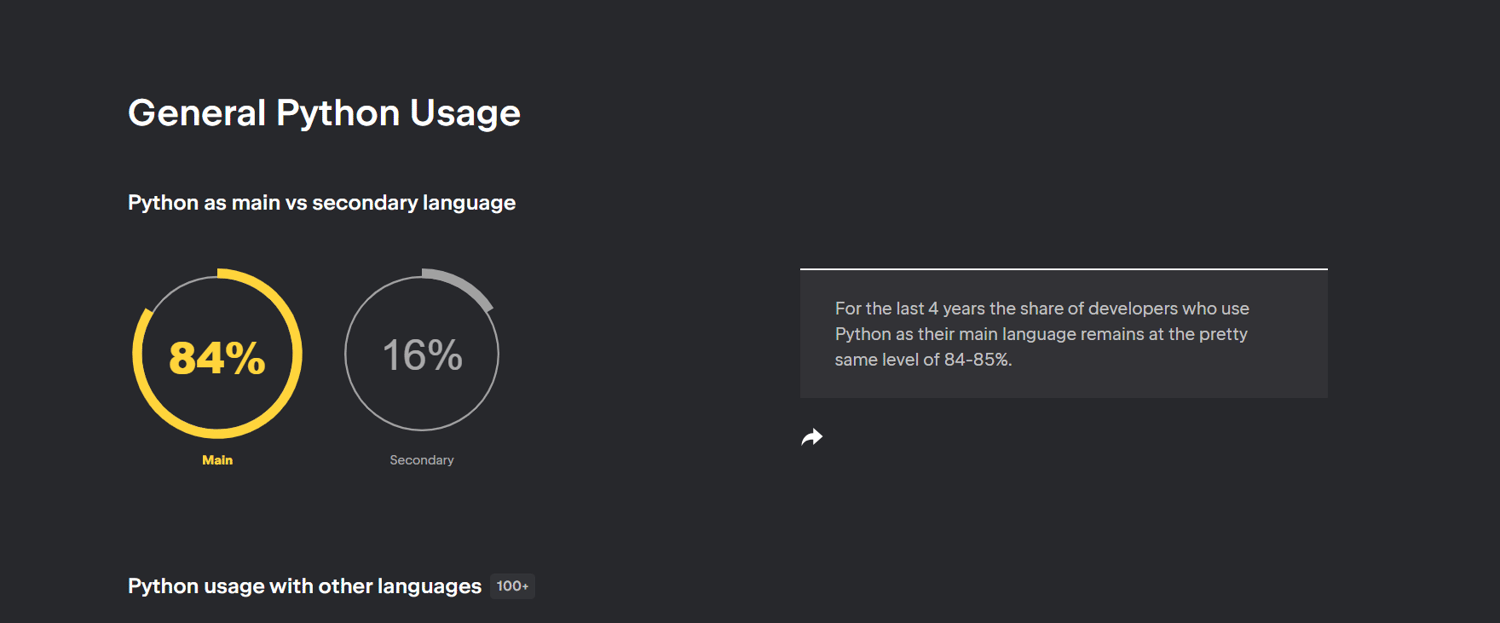
According to the fifth Python Developers Survey results, 84% of developers consider Python their Main language, and 16% believe it is their secondary one! This figure reflects Python’s popularity among developers, organizations, startups, and young professionals.
But! This doesn’t make me relax since popularity also brings many risks and threats. I hope the developers know that python core is secure, but third-party modules may not. Therefore, to solve this issue, you need a security scanner to find vulnerabilities.
There are many comprehensive online security scanners to test for online threats, but they may be unable to detect platform-specific weaknesses like Python and Node.js. Etc.
Let’s delve into the list of best scanning tools that finds security risks and vulnerabilities in a Python application.
PYT (Python Taint)
An open source static analysis tool to detect command injection, cross-site scripting, SQL injection, directory transversal attacks in Python web applications.
PYT is based on the theoretical foundation, and if you would like to contribute, then you can join their slack group.
Bandit
Bandit is an Open Stack’s initiative to find common security risk in python code. It processes each file to build AST and generate a report.
You can get it installed using pip.
The usage of Bandit can be customized. For an ex, by default test is done against all the profile, however, if you want to check just ShellInjection then you can try below.
bandit samples/*.py -p ShellInjection
You may also instruct to report based on severity (Low, Medium or High) level.
Safety
Safety is a Python dependencies checker that can scan the local virtual environment, requirements file, and stdin inputs for security issues.

From building pipelines to production systems, Safety CLI can be used in various situations. Trust me! If you have any vulnerabilities or security threats to your Python Application, Safety CLI will detect them with ease. It will also ensure you have full details regarding the scan; therefore, it generates a report on the existing threats and vulnerabilities to make your job easier.
PyUp
Keep your Python application up-to-date, compliant, and secure with PyUp’s Python Dependency Security. It helps you secure your code from thousands of security vulnerabilities in Python dependencies that can breach your Python code.

Instead of spending your time manually updating and tracking each dependency, you can get PyUp to automate tasks. It fixes new vulnerabilities automatically and allows you to stay away from known vulnerabilities to boost your confidence in your code.
Furthermore, PyUp maintains a database of vulnerabilities, and to date, it has recorded 472,750 Python dependencies. Its scanners are built for solving complex environments and scanning your files for outdated and insecure requirements.
These scanners are also highly configurable according to your needs, and their safety CI catches vulnerabilities before the code goes to production. Integrate command-line tools in your CI workflows.
Get unlimited public and private repositories at $249/month and avail dependency licenses, CVSS, API key, and safety CI.
Snyk
In the middle of this exciting brawl, I would like to introduce Snyk. Snyk Open Source delivers software configuration analysis (SCA). Snyk gives you the liberty to find vulnerable dependencies, Scan pull appeals before merging, Prevent new vulnerabilities from coming into action, and you can test your production environment in concern of existing vulnerabilities and issues.

These features alone make Snyk an excellent option for developers. You have the opportunity to Scan, Monitor, Fix, and Automate. You can use a broad application context to prioritize open-source issues that are reachable, deployed, or publicly exposed. I have listed some features that may give you clarity regarding Snyk,
- Snyk can automate vulnerability fixes.
- Snyk gives you mental peace by automatically monitoring your deployed Python code for vulnerabilities.
- Continuously assess compliance with regulatory and internal security policies.
- Snyk is specially molded for security engineers and GRC teams.
Overall, I feel Snyk is the correct claimant for a position in our list, and developers should go for Snyk once to find security vulnerabilities in their applications.
Soos.io
Soos SCA claims to be the low-cost, all-in-one solution for everything you need in an SCA. And believe me; the claim is not hollow! Some significant features which helped Soos SCA to reach this list are given below,
- Fastest Implementation.
- Ease of use! A practical UX.
- Easy to set up and proceed towards scanning vulnerabilities.
- A great performer.
And all these affordable options indicate that this tool will meet any developer’s expectations when finding security vulnerabilities in your Python Application. It offers unlimited scans whenever you want. This feature allows developers to get to the end.
Another feature that caught my attention is its ranking algo; I found vulnerabilities are ranked by severity, impact, and exploitability.
The most attractive feature, which made me go crazy behind this tool, is its rich dashboard. It’s imposing when it comes to fetching the information, and it becomes too handy for you as well to proceed with. All-Inclusive, it’s a beautiful package to eliminate the threats surrounding your Python Application.
Pyre
Pyre is an excellent tool to find or detect security vulnerabilities. The reason I am calling it a perfect tool is because it has the capacity to analyze codebases with millions of lines of code.

It has some role in your efficiency as it provides instantaneous feedback and reports to developers parallelly as they write code. Pyre includes Pysa, a security-focused static analysis tool built on top of Pyre. Pysa analyzes data flows in Python applications.
The initial configuration includes some simple steps. First, you need to set up the virtual environment, install Pyre and SAPP in the virtual environment, and finally, initialize Pysa and SAPP.
Don’t forget! SAPP is crucial to execute the analysis. You can quickly setup a suitable environment to run Pysa and SAPP with the following command:
(pysa) $ pyre init-pysa
This command will configure your repo to run Pysa. And then proceed towards running Pysa and SAPP with the following commands,
(pysa) $ pyre analyze --no-verify --save-results-to ./pysa-runs
(pysa) $ sapp analyze ./pysa-runs/taint-output.json
Overall this tool will help you greatly; It has earned a spot with its positive tilt toward Python. Therefore, don’t hesitate and go ahead for Pyre without thinking twice!
Trivy
I introduce you to “Trivy”, an exceptional, versatile, and comprehensive security scanner. More surprisingly, it has a special love for Python that made it possible for Trivy to reach the list.

Trivy can scan container images, filesystem, Git Repository, AWS, etc. Trivy supports other popular languages besides Python, such as Ruby, Node.js, Java, etc. It can also support operating systems.
There are several options regarding installation; some of the popular ones are mentioned below to proceed with,
brew install trivydocker run aquasec/trivy- Options to download the binary from the aquasecurity main page are also available.
To end this, I would like to highlight an essential aspect of Trivy; it can be integrated with many popular platforms and applications like Kubernetes Operator and VS Code Plugin.
Final Words
Coming down to the conclusion, you must be curious about my personal preference. I believe there are several practical tools to find vulnerabilities in Python Applications. All the tools mentioned above in the list have their offerings. To be accurate, all are great options.
Each tool brings unique advantages to enhance the security of your Python code. I would suggest considering your specific requirements and preferences when making your selection.
Next, check out the best Python frameworks for building small to enterprise applications.


















