As a web application owner, how do you ensure your site is protected from online threats? Doesn’t leak sensitive information?
An interesting report by Symantec reveals 1 out of 10 websites had one or more malicious code.
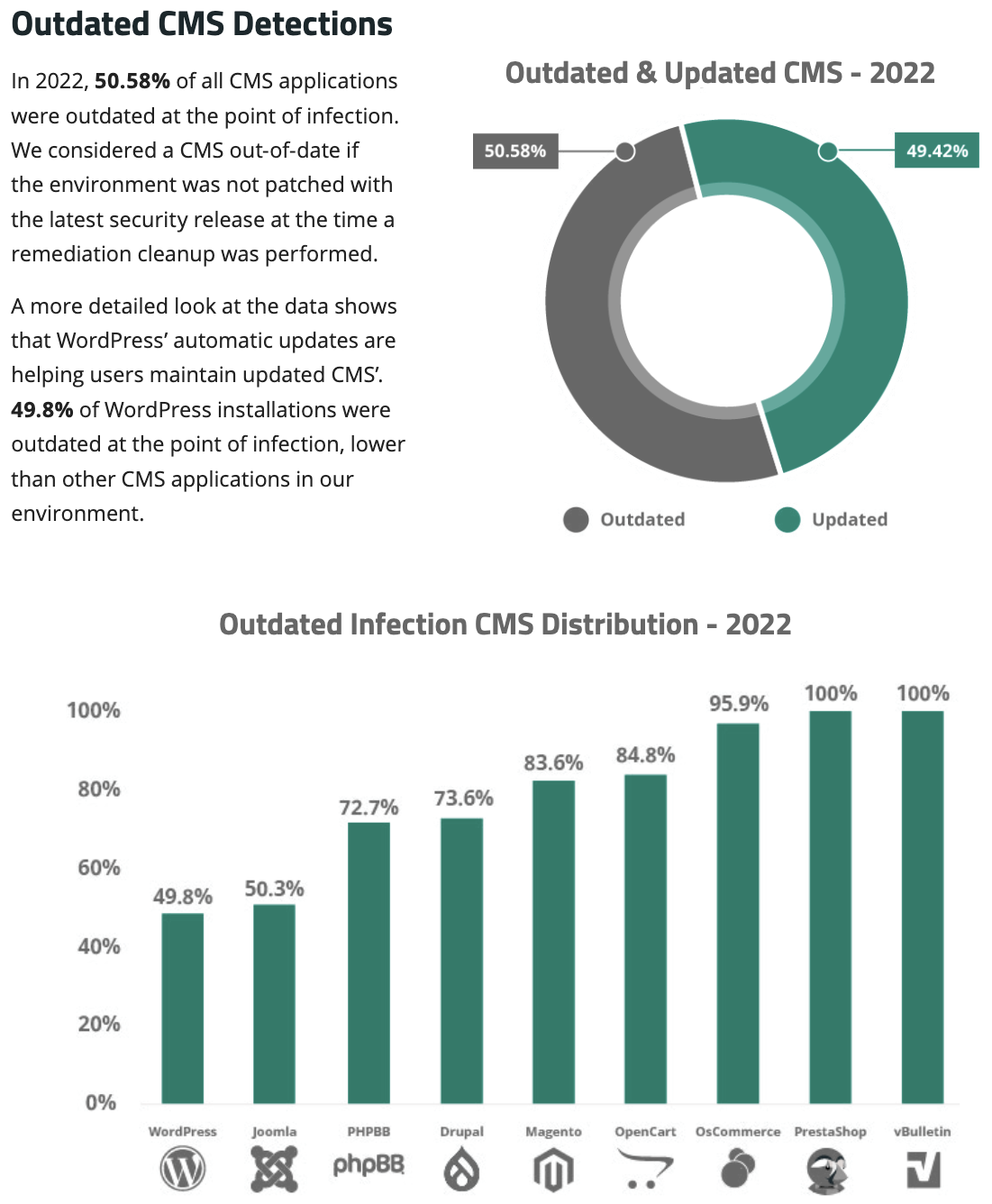
And, if you are using WordPress, then another report by SUCURI shows 49.8% of scanned websites were outdated.
If you are using a cloud-based security solution, then most likely, regular vulnerability scanning is part of the plan. However, if not, then you got to perform a routine scan and take necessary action to mitigate the risks.
There are two types of scanners.
Commercial – give you the option to automate the scanning for continuous security, reporting, alerting, detailed mitigation instructions, etc. Some of the known names in the industry are:
- Acunetix
- Detectify
- Qualys
Open Source/Free – you can download and perform a security scan on-demand. Not all of them will be able to cover a broad range of vulnerabilities like a commercial one.
Let’s check out the following open-source web vulnerability scanner.
dirsearch
‘dirsearch‘ is a popular web directory and file enumeration tool used for discovering hidden directories & files on a web server.

It is a command-line tool written in Python and often used by penetration testers to identify misconfigurations & sensitive files that should not be publicly accessible.
Features
- Directory Brute-Forcing
- Custom Wordlists
- HTTP Methods Support
- Extension Detection (can check for files with specific extensions like .php, .txt, .html, etc.)
- Concurrent Requests to speed up the enumeration process.
- Positive/Negative Match Filtering
- uses recursive Mode to search for files.
It works by sending a series of HTTP requests to the target web server and then trying to access a predefined list of common directories.
If any file is found – dirsearch will report it, which indicates that the file may be accessible to the public.
reNgine
reNgine is an advanced web application recon tool designed to assist penetration testers in identifying potential vulnerabilities and the attack surface of web applications.

It provides a highly customizable & powerful scanning capability through its Engines, which allows users to configure and fine-tune the scanning process according to their needs.
Features
- Highly Configurable Scan Engines
- Recon Data Correlation
- Continuous Monitoring to make sure the security posture of the application remains up-to-date.
- Database-Backed Recon Data to access and analyze the results whenever the user wants.
- Simple User Interface
And also, the Sub-Scan & Deeper Correlation feature allows users to scan specific parts of the application or individual components separately.
w3af
w3af (Web Application Attack & Audit Framework), an open-source project, started back in late 2006. w3af is written in Python and allows users to discover and exploit various security issues, including OWASPs.

The primary goal of w3af is to assist security testers and developers in strengthening the security of web applications.
And here is a list of vulnerabilities that w3af can scan.
Features
- Users can create plugins and scripts based on their specific needs.
- It can also operate in HTTP proxy mode that allows users to intercept and modify HTTP transactions.
- Generate detailed reports on the identified vulnerabilities and the steps taken during the testing process.
It’s built on a plugin architecture, and you can check out all the plugins available here.
Nikto
Nikto is an open-source (GPL) scanner that is designed to perform complete tests against web servers to identify security vulnerabilities and configuration issues.
Nikto identifies web servers and software running on the target server, which gives administrators a better understanding of their system’s setup.
Features
- Support for SSL & full HTTP proxy.
- Customizable reports using a template engine.
- Ability to scan multiple ports on a server or multiple servers via an input file
- Scan tuning to include or exclude entire classes of vulnerability checks.
- Enhanced false-positive reduction using various methods like headers, page content, and content hashing.
- Host authentication with Basic and NTLM methods.
Nikto is not designed to be a stealthy tool – as it aims to test web servers as quickly as possible. Its activities are often visible in log files or in IPS/IDS systems. But it supports LibWhisker’s anti-IDS methods, which can help users test their IDS systems or attempt to evade detection in specific scenarios.
And here is an article on how to use the Nikto scanner to find web server vulnerabilities. Feel free to visit this page.
Wfuzz
Wfuzz (Web Fuzzer) is an application assessment tool for penetration testing. You can fuzz the data in the HTTP request for any field to exploit and audit the web applications.

It also supports brute-force attacks by allowing users to test multiple values for specific parameters. This can be particularly useful for discovering weak credentials or sensitive information that might be exposed through incorrect configurations.
Features
- Payload customization & Fuzzing capabilities that fuzz different parts of HTTP requests, including parameters, headers, and cookies, to identify weaknesses in input validation.
- Wfuzz is built as a modular framework. So it will be easy for developers to create & integrate custom plugins.
- HTTP Header and Authentication Testing
- Wfuzz can be integrated with other security tools, such as Burp Suite. It allows users to make use of previous HTTP requests & responses from other tools.
It can also perform directory and file fuzzing to identify sensitive files and other resources on the web server.
OWASP ZAP
OWASP ZAP (Zed Attack Proxy) is a popular open-source web app security scanner and penetration testing tool. It is free to use and actively maintained by the OWASP community, which makes it a reliable choice for securing web applications.

It’s a cross-platform Java-based tool that can run even on Raspberry Pi. ZAP sits between a browser and a web application to intercept & inspect messages.
Features
- ZAP has a spidering functionality that helps identify and map out all accessible endpoints within the target web application.
- Automated Scanning
- It supports manual testing by providing an interactive proxy. Users can intercept & modify requests between the client and the server.
- ZAP supports fuzzier plugins to fuzz-test various inputs of the target application to discover potential vulnerabilities.
And also it can be integrated into the development & testing process through its API. We highly recommend checking out OWASP ZAP tutorial videos to get started.
Wapiti
Wapiti is another powerful web application vulnerability scanner to assess the security of their websites.

It operates as a “black-box” scanner – which means it doesn’t require access to the application’s source code. Instead, it analyzes the deployed web application by crawling its web pages & looking for potential vulnerabilities.
Features
- Vulnerability Coverage includes file disclosure detection, XXE (XML eXternal Entity) injection, CRLF injection, open redirects, and more.
- HTTP Methods and Payload Injection
- Supports HTTP/HTTPS/ SOCKS5 proxies and allows authentication via Basic, Digest, NTLM, or GET/POST on login forms.
- Users can activate or deactivate SSL certificate verification during the scan.
- Imports cookies from Chrome or Firefox browsers and supports MITM proxy to explore the target using the user’s browser.
Wapiti offers several options to control the behavior of the crawler, such as skipping specific parameter names during the attack, setting a maximum time for the scan process, adding custom HTTP headers, and more.
Vega
Vega is developed by Subgraph – a multi-platform supported tool written in Java to find XSS, SQLi, RFI, and many other vulnerabilities. The built-in automated scanner is designed for quick and efficient security tests.
It can crawl through web applications, scan for various vulnerabilities, and report the findings to the user.
Features
- The Intercepting Proxy feature can perform SSL interception for HTTP websites & analyze encrypted traffic.
- Multi-Platform Support
- The proxy can be configured to run attack modules while the user is browsing the target site.
If you are a developer, you can leverage Vega API to create new attack modules.
SQLmap
SQLmap is an open-source pentesting tool that automates the process of detecting & exploiting SQL injection vulnerabilities in web applications.
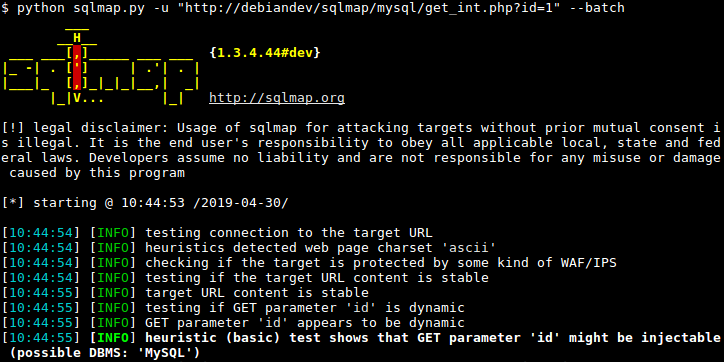
This tool evaluates the application’s responses and constructed requests in order to find potential injection points.
Features
- DBMS Support, including MySQL, Oracle, PostgreSQL, SQLite, and many others.
- Enumeration of Database Information
- Supports various SQL injection techniques such as boolean-based blind, time-based blind, error-based, and UNION query-based.
- Direct Database Connection
- Password Hash Cracking
- Data Dumping
- Arbitrary Command Execution on an underlying operating system for supported systems.
And also it can extract information about the DBMS being used such as its type, version, and configuration details. This helps testers understand the environment they are dealing with.
Grabber
Grabber is a simple & portable scanner designed to detect vulnerabilities in small websites such as personals and forums but it’s not meant for large applications.
Features
- JavaScript source code analyzer
- Cross-site scripting, SQL injection, Blind SQL injection
- PHP application testing using PHP-SAT
Grabber only identifies the vulnerabilities and doesn’t provide solutions. After the detection, it generates a file with the session ID & timestamps for future statistical analysis.
Conclusion
Web security is critical to any online business, and I hope the above-listed free/open-source vulnerability scanner helps you to find risk so you can mitigate it before someone take advantage of it. If you are interested in learning about penetration testing, then check out this online course.
You may also read some best tips to avoid common web security vulnerabilities.

















